The main purpose of Multi-Factor Authentication (MFA) is to prevent the abuses of the user accounts. In practice MFA means that you verify, in other words approve your sign-ins on the phone, which has been connected with MFA. Because your phone is needed for the verification, no external quarter is able to abuse your user account.
The verification by phone is required when logging with universities M365 account.
MFA is in use for all the Microsoft accounts aka M365/O365 usernames of the university and Oamk. In practice, MFA is connected to the user accounts of the staff and students and also to the so-called UFO accounts. The MFA is also in use for the guests who have been invited to Teams groups, read more: MFA with a guest user account (ict.oulu.fi)
If your MS account doesn’t include the setting, how to send an verification request to you, you will be directed by the notification “More information required” (in Finnish “Lisätietoja tarvitaan”) to add your verification method to your MS account’s security information.
The contents of this instruction:
- Setting up Authenticator
- Alternative authentication method (FIDO2)
- Resetting Authenticator
- Use of MFA
- FAQ
Setting up Authenticator
Microsoft Authenticator
Choose Microsoft Authenticator application as your default method if you are using a smartphone. Microsoft Authenticator is the preferred method of verification. Its use makes it possible to take advantage of some new features, for example reset the password without Suomi.fi authentication.
Do this:
- Download Microsoft Authenticator from the app store of your phone (Android / iOS).
- Do this on your computer:
- Sign in at https://o365.oulu.fi (link opens in a new window)
- You should see a “Lets keep your account secured“ notification, press Next.
- Press Next and you should now see a QR code.
- Open the Microsoft Authenticator app on your phone and allow notifications and camera use.
- In the top right you should see a + button, press on it and after that select Work or school account and Scan QR code.
- Scan the QR code and press Next.
- In the Authenticator app you should now see a “Are you trying to sign in?” pop up, type in the numbers you see in the sign-in window in your browser and press Yes. Go back into your browser and press Next.
- Authenticator is now set up on your account, press Done.
- If you didn’t get the “Lets keep your account secured“ notification and are instead directly logged in to the o365 portal:
- Open your account settings through the Profile menu in the bottom left corner by selecting View account
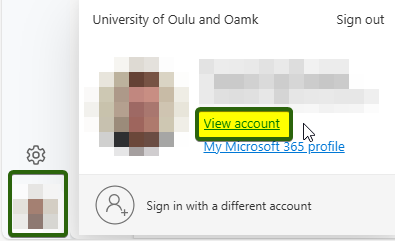
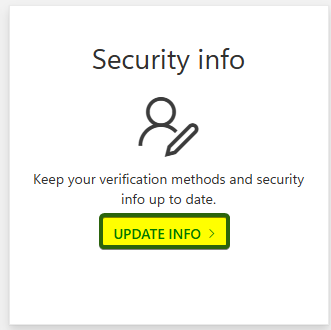
Optionally you can access Security info directly from this link: https://mysignins.microsoft.com/security-info - Open Security info by clicking on Update info
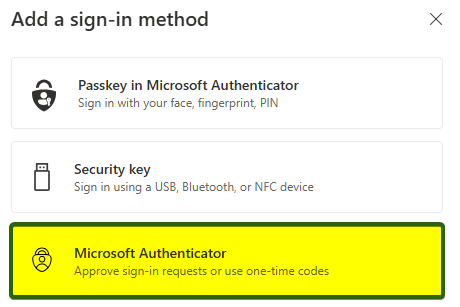
- Click on + Add sign-in method and then select Microsoft Authenticator
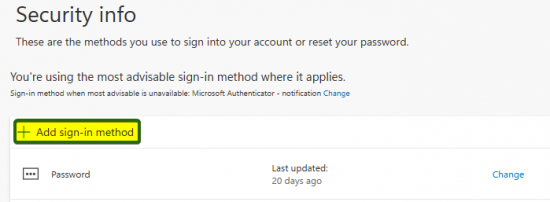
You can remove your previous authentication method from the list below the + Add sign-in method button
- Open your account settings through the Profile menu in the bottom left corner by selecting View account
- Please choose Microsoft Authenticator as a primary method. From now on, you will accept or deny the verification requests on the Microsoft Authenticator application that has been installed in your mobile device.
- The phone must have a data connection and the device should be available to you.
- If you process the university email or calendar also on the same mobile device, the application must be Outlook or some other application which supports the feature Modern Authentication of M365.
- You can also use the Authenticator app to authenticate other, including your private user accounts, by adding the accounts you like in the app.
Authenticator allows you to make use of passwordless sign-in.
Detailed instructions on how to take MFA in use (PDF)
Alternative authentication method (FIDO2)
If you cannot or do not want to use the mobile app for authentication, you can alternatively use a FIDO2 key. The FIDO2 key most commonly works with a USB connection, and it costs approximately 50-100 euros. The FIDO2 key works on a laptop or desktop computer with a USB connection.
The staff can obtain the key from Netox, discuss the matter with the person in charge of purchasing your unit.
The key used in the instructions is the Identiv uTrust FIDO2 NFC key.
Note! Setting up the FIDO2 key requires that you have first set up the Authenticator.
- Connect the security key to your device.
- Go to: https://aka.ms/security-info and click + Add sign-in method.
- Select Security Key.
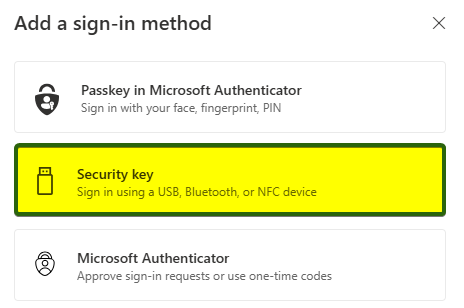
- You may have to verify your login with Authenticator, click Next.
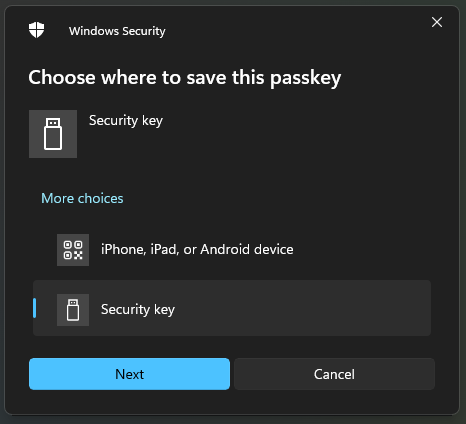
- Select NFC device and press Next.
- In the Windows Security window that opens, select Security Key and press Next.
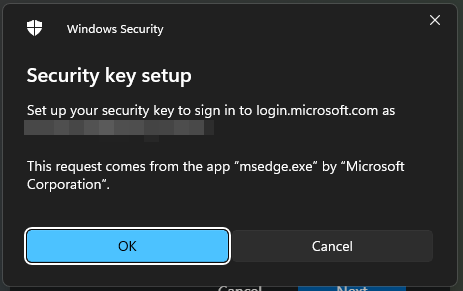
- In the next two windows, simply press OK.
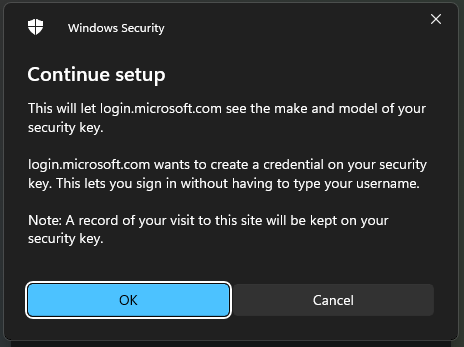
- Input a PIN code of your choice and press OK.
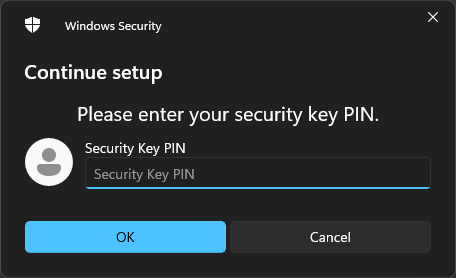
In this image a PIN code has already been set.
- Your security key will now light up, touch it.
- Press OK, you will be returned to the Security info page.
- Name your device, e.g. uTrust FIDO2 and click OK. You can now use your security key to authenticate your sign ins.
Resetting and reconfiguring Authenticator
If you have uninstalled or reinstalled the Authenticator app, reset your phone or acquired a new phone, you will need to set up Authenticator again.
- Go to https://account.oulu.fi/mfa and authenticate using your Finnish online banking credentials.
- If you are unable to authenticate via the suomi.fi service, please contact ict@oulu.fi or visit the ICT service point at the Linnanmaa campus in room KE1020.
- Click the Get temporary pass code button to receive a temporary code that you can use to log in. Then click the link https://mysignins.microsoft.com/security-info.
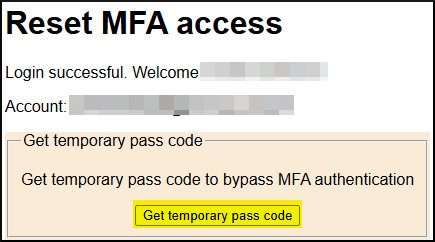
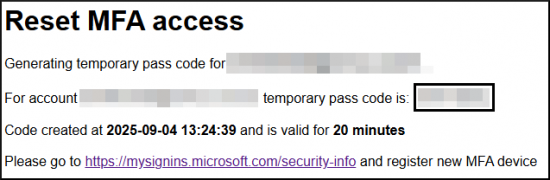
images from the MFA service
- You can now follow the Setting up Authenticator instructions starting from step 3.
- For now, it is still possible to use the text message (SMS) option to receive the temporary code, however this will be discontinued.
Use of MFA
- Once your MS account includes a working verification method, requests for verification will be coming to the Authenticator app on your phone.
- Verification requests apply only to those logins where you use the university’s M365 user name. Requests come both inside and outside the network.
- In the future, the need for verification will decrease as trust relationships arise with the devices you use.
- In the login window, you can choose a secondary verification method if the primary method cannot be used at that moment. Because of this, it is recommended to have at least two working methods stored in your security info.
FAQ
If in the introduction any problems or questions arise, please check if the solution is found here: FAQ – Frequently Asked Questions.
- You can contact Campus ICT support service too.